AWS Solution Architect(Associate) - Topic 4: Advanced IAM
AWS Identity and Access Management (IAM) enables you to manage access to AWS services and resources securely.
Using IAM, you can create and manage AWS users and groups, and use permissions to allow and deny their access to AWS resources.

[toc]
Advanced IAM
AWS Directory Service
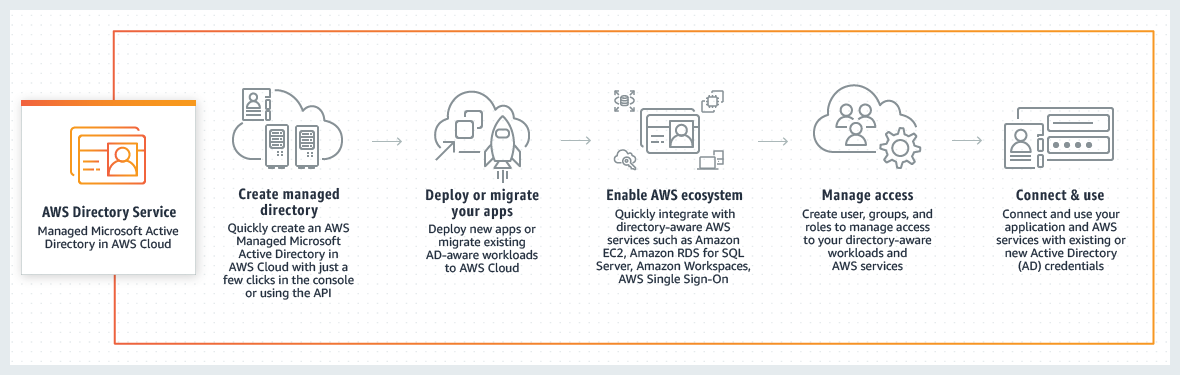
AWS Directory Service for Microsoft Active Directory, also known as AWS Managed Microsoft Active Directory (AD), enables your directory-aware workloads and AWS resources to use managed Active Directory (AD) in AWS.
https://aws.amazon.com/rds/faqs/
| AWS | Customer |
|---|---|
| Multi-AZ Deployment | Users, Groups, GPOs |
| Patch, Monitor, Recover | Standard AD Tools |
| Instance Rotation | Scale out DCs |
| Snapshot and Restore | Trusts (Resource Forest) |
| Certificate Authorities | |
| Federation |
User Case
- Provide your on-premises AD users quick access to AWS
- Leverage integrations with Amazon RDS and Amazon FSx
- Enable single sign-on experience for AWS End User Computing services
- Give your on-premises AD users federated access to the AWS Management Console and AWS CLI quickly
- Grant your on-premises AD users single-click access to cloud business applications
| AD Compatible | Not AD Compatible |
|---|---|
| Managed Microsoft AD | Cloud Directory |
| AD Connector | Cognito User Pools |
| Simple AD |
Simple AD
- Standalone managed directory
- Basic AD features
- Small: <= 500; Large <= 5000 users
- Easier to manage EC2
- Linux workloads that need LDAP
- Does not support trusts (can’t join on-promises AD)
AD Connector
- Directory gateway (proxy) for on-premises AD
- Avoid caching information in the cloud
- Allow on-premises users to log in to AWS using AD
- Join EC2 instances to your existing AD domain
- Scale across multiple AD Connectors
Cloud Directory
- Directory-based store for developers
- Multiple hierarchies with hundreds of millions of objects
- Use cases: org charts, course catalogs, device registries
- Full managed service
Amazon Cognito User Pools
- Managed user directory for SaaS application
- Sign-ip and sign-in for web or mobile
- Works with social media identities
IAM Policies
Amazon Resource Name (ARN)
begin with: arn:partition:service:region:account_id
IAM Policies
Not explicitly allowed == implicity denied
- JSON document that defines permissions
- Identity Policy & Resource Policy
- No effect until attached
- List of Statements (Effect/Action/Resource)
Permission Boundaries
- Used to delegate administration to other users
- Prevent privilege escalation or unnecessarily broad permissions
- Control maximum permissions an IAM policy can grant
- Use Cases
- Developers creating roles for Lambda functions
- Application owners creating roles for EC2 instances
- Administrator creating ad hoc users
AWS Resource Access Manager (RAM)
RAM eliminates the need to create duplicate resources in multiple accounts, reducing the operational overhead of managing those resources in every single account you own.

You can create resources centrally in a multi-account environment, and use RAM to share those resources across accounts in three simple steps: create a Resource Share, specify resources, and specify accounts. RAM is available to you at no additional charge.
AWS Single Sign-On
Centrally manage access to multiple AWS accounts and business applications and provide users with single sign-on access to all their assigned accounts and applications from one place.

AWS Solution Architect(Associate) - Topic 4: Advanced IAM
http://vincentgaohj.github.io/Blog/2021/01/08/AWS-Solution-Architect-Associate-4-Advanced-IAM/