AWS Solution Architect(Associate) - Topic 6: VPCs
Virtual Private Cloud (AWS Amazon) lets you provision a logically isolated section of the Amazon Web Services Cloud where you can launch AWS resources in a virtue network that you define.
You have complete control over your virtual networking environment, including selection of your own IP address range, creation of subnets, and configuration of route tables and network gateways.

VPCs
Virtual Private Cloud lets you provision a logically isolated section of the Amazon Web Services Cloud where you can launch AWS resources in a virtue network that you define. You have complete control over your virtual networking environment, including selection of your own IP address range, creation of subnets, and configuration of route tables and network gateways.
VPC Overview
No Translative peering
When you create a VPC, a default Route Table, Network Access Control List and a default Security Group is created
It won’t create any subnets, nor will it create a default Internet gateway
Amazon always reserve 5 IP addresses within your subnets
You can only have 1 Internet Gateway per VPC
Security Groups cant span VPCs.
Amazon Virtual Private Cloud features
Amazon Virtual Private Cloud provides features that you can use to increase and monitor the security for your virtual private cloud (VPC):
Reachability Analyzer: Reachability Analyzer is a static configuration analysis tool that enables you to analyze and debug network reachability between two resources in your VPC.
VPC Flow Logs: You can monitor your VPC flow logs delivered to Amazon S3 or Amazon CloudWatch to gain operational visibility into your network dependencies and traffic patterns, detect anomalies and prevent data leakage, or troubleshoot network connectivity and configuration issues.
VPC Traffic Mirroring: VPC traffic mirroring allows you to copy network traffic from an elastic network interface of Amazon EC2 instances and then send the traffic to out-of-band security and monitoring appliances for deep packet inspection.
Ingress Routing: This allows you to route all incoming and outgoing traffic flowing to/from an Internet Gateway (IGW) or Virtual Private Gateway (VGW) to a specific EC2 instance’s Elastic Network Interface. With this feature, you can configure your virtual private cloud to send all traffic to an IGW, VGW or EC2 instance before the traffic reaches your business workloads.
Security Groups: Security groups act as a firewall for associated Amazon EC2 instances, controlling both inbound and outbound traffic at the instance level.
Network Access Control List: A network access control list (ACL) is an optional layer of security for your VPC that acts as a firewall for controlling traffic in and out of one or more subnets.
Security groups vs Network ACLs
| Security group | Network ACL |
|---|---|
| Operates at the instance level | Operates at the subnet level |
| Supports allow rules only | Supports allow rules and deny rules |
| Is stateful: Return traffic is automatically allowed, regardless of any rules | Is stateless: Return traffic must be explicitly allowed by rules |
| We evaluate all rules before deciding whether to allow traffic | We process rules in order, starting with the lowest numbered rule, when deciding whether to allow traffic |
| Applies to an instance only if someone specifies the security group when launching the instance, or associates the security group with the instance later on | Automatically applies to all instances in the subnets that it’s associated with (therefore, it provides an additional layer of defense if the security group rules are too permissive) |
Network Address Translation (NAT)
NAT Instance
- When creating a NAT instance, Disable Source/Destination Check on the Instance
- NAT instances must be in a public subnet
- There must be a route out of the private subnet to the NAT instance, in order for this to work
- The amount of traffic that NAT instances can support depends on the instance size. If you are bottlenecking, increase the instance size.
- You can create high availability using auto-scaling Groups, multiple subnets in different AZs, and a script to automate fail-over.
NAT Gateways
If you have resources in multiple Availability Zones and they share one NAT gateway, in the event that the NAT gateway’s Availability Zone is down, resources in the other Availability Zones lose Internet access. To create an Availability Zone-independent architecture, create a NAT gateway in each Availability Zone and configure your routing to ensure that resources use the NAT gateway in the same Availability Zone.
- Redundant inside the Availability Zone
- Preferred by the enterprise
- Starts at 5 Gbps and scales currently to 45 Gbps
- No need to patch
- Not associated with security groups
- Automatically assigned a public ip address
- Remember to update your route tables
- No need to disable Source/Destination Checks
Access Control Lists (ACL)
VPC automatically comes with a default network ACL, and by default it allows all outbound and inbound traffic
You can create custom network ACLs. By default, each custom network ACL denies all inbound and outbound traffic until you add rules.
Each subnet in your VPC must be associated with a network ACL. If you don’t explicitly associate a subnet with a network ACL, the subnet is automatically associated with the default network ACL
Block IP Addresses using network ACLs not Security Groups
You can associate a network ACL with multiple subnets; however, a subnet can be associated with only one network ACL at a time. When you associate a network ACL with a subnet, the previous association is removed.
Network ACLs contain a numbered list of rules that is evaluated in order, starting with the lowest numbered rule.
Network ACLs have separate inbound and outbound rules, and each rule can either allow or deny traffic
Network ACLs are stateless; responses to allowed inbound traffic are subject to the rules for outbound traffic (and vice versa.)
VPC Flow Logs
- You cannot enable flow logs for VPCs that are peered with your VPC unless the peer VPC is in your account.
- You can tag flow logs
- After you’ve created a flow log, you cannot change its configuration; for example, you can’t associate a different IAM role with the flow log
Not all IP traffic is monitored
- Traffic generated by instances when they contact the Amazon DNS server. If you use your own DNS server, then all traffic to that DNS server is logged
- Traffic generated by a Windows instance for Amazon Windows license activation
- Traffic to and from
169.254.169.254for instance meta-data - DHCP (Dynamic Host Configuration Protocol) traffic
- Traffic to the reserved IP address for the default VPC router
Bastions
A bastion host can be thought of as a special purpose machine, which has been configured to work against attacks. The machine contains a single application only, which it hosts. It has access to the public network, and it also known as a ‘Jump Box’. It is a powerful server, which provides high-level network security, since it is the only host that is granted permission to access the public network.
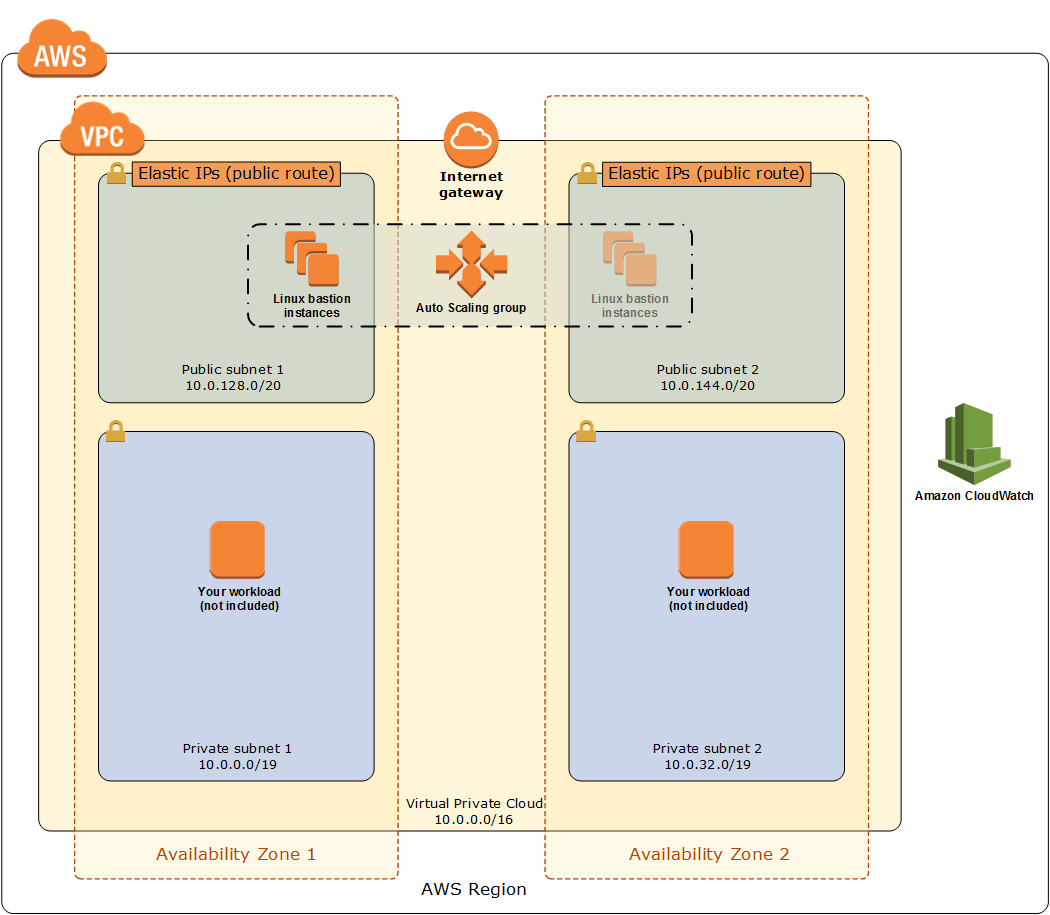
A NAT Gateway or NAT Instance is used to provide Internet traffic to EC2 instances in a private subnets
A Bastion is used to securely administer EC2 instances (Using SSH or RDP). Bastions are called Jump Boxes in Australia
You cannot use a NAT Gateway as a Bastion host
Direct Connect
Basic Idea
AWS Direct Connect is a cloud service solution that makes it easy to establish a dedicated network connection from your premises to AWS. Using AWS Direct Connect, you can establish private connectivity between AWS and your data-center, office, or co-location environment, which in many cases can reduce your network costs, increase bandwidth throughput, and provide a more consistent network experience than Internet-based connections.

- Direct Connect directly connects your data center to AWS
- Useful for high throughput workloads (for example, lots of network traffic)
- Or it you need a stable and reliable secure connection
Steps to Creating a Direct Connect Connection
- Create a virtual interface in the Direct Connect console. This is a PUBLIC Virtual Interface
- Go to the VPC console and then to VPC connections. Create a Customer Gateway
- Create a Virtual Private Gateway
- Attach the Virtual Private Gateway to the desired VPC
- Select VPN Connections and create new VPN Connection
- Select the Virtual Private Gateway and the Customer Gateway
- Once the VPN is available, setup the VPN on the customer gateway or firewall
Niches Topic of SAA-C02
Global Accelerator
AWS Global Accelerator is a networking service that sends your user’s traffic through Amazon Web Service’s global network infrastructure, improving your internet user performance by up to 60%. When the internet is congested, Global Accelerator’s automatic routing optimizations will help keep your packet loss, jitter, and latency consistently low.
- AWS Global Accelerator is a service in which you create accelerators to improve availability and performance of your applications for local and global users.
- You can assigned two static IP addresses (or alternatively you can bring your own)
- You can control traffic using traffic dials. This is done within the endpoint group.
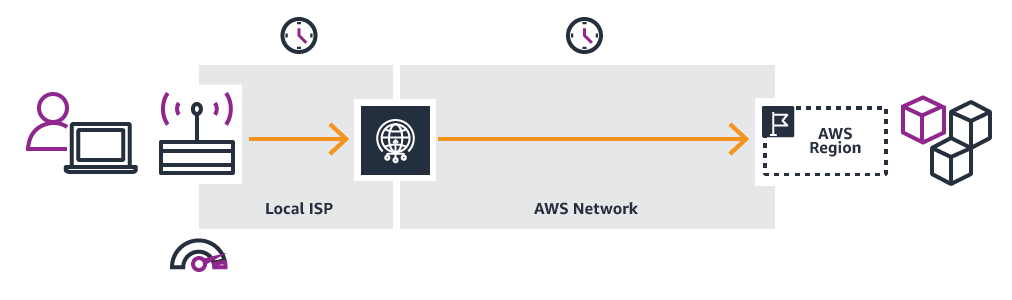
With AWS Global Accelerator:
Adding AWS Global Accelerator removes these inefficiencies. It leverages the Global AWS Network, resulting in improved performance.
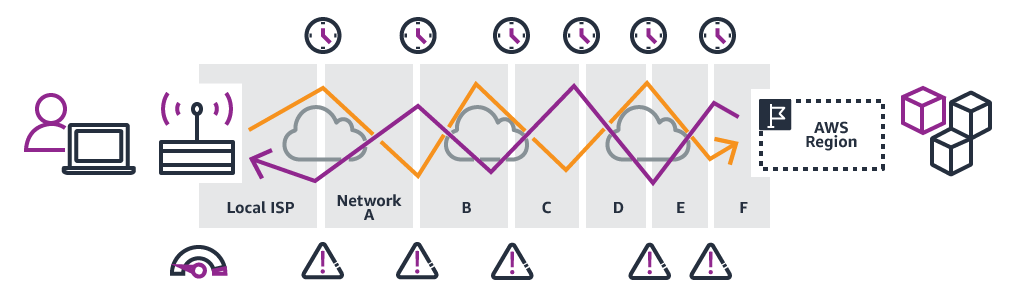
Without AWS Global Accelerator:
It can take many networks to reach the application. Paths to and from the application may differ. Each hop impacts performance and can introduce risks.
AWS Global Accelerator Components
Static IP addresses
- By default, Global Accelerator provides you with two static IP addresses that you associate with your accelerator.
1.2.3.4/5.6.7.8
Accelerator
- An accelerator directs traffic to optimal endpoints over the AWS global network to improve the availability and performance of your Internet applications.
- Each accelerator includes one or more listeners
DNS Name
- Global Accelerator assigns each accelerator a default Domain Name System(DNS) name – that points to the static IP addresses that Global Accelerator assigns to you.
- Depending on the use case, you can use your accelerator’s static IP addresses or DNS name to route traffic to your accelerator, or set up DNS records to route traffic using your own custom domain name.
Network Zone
- A network zone services the static IP addresses for your accelerator from a unique IP subnet. Similar to an AWS Availability Zone, a network zone is an isolated unit with its own set of physical infrastructure.
- When you configure an accelerator, by default, Global Accelerator allocates two IPv4 addresses for it. If one IP address from a network zone becomes unavailable due to IP address blocking by certain client networks, or network disruptions, client applications can retry on the healthy static IP address from the other isolated network zone.
Listener
- A listener processes inbound connections from clients to Global Accelerator, based on the port (or port range) and protocol that you configure. Global Accelerator supports both TCP and UDP protocols.
- Each listener has one or more endpoint groups associated with it, and traffic is forwarded to endpoints in one of the groups.
- You associate endpoint groups with listeners by specifying the Regions that you want to distribute traffic to.
- Traffic is disputed to optimal endpoints within the endpoint groups associated with a listener.
Endpoint Group
- Each endpoint group is associated with a specific AWS Region
- Endpoint groups include one or more endpoints in the Region
- You can increase or reduce the percentage of traffic that would be otherwise directed to an endpoint group by adjusting a setting called a traffic dial
- The traffic dial lets you easily do performance testing or blue/green deployment testing for new releases across different AWS Regions, for example.
Endpoint
- Endpoints can be Network Load Balancers, Application Load Balancers, EC2 instances, or Elastic IP addresses
- An Application Load Balancer endpoint can be an Internet-facing or internal. Traffic is routed to endpoints based on configuration options that you choose, such as endpoint wrights
- For each endpoint, you can configure weights, which are numbers that you can use to specify the proportion of traffic to route to each one. This can be useful, for example, to do performance testing within a Region.
VPC End Points
Amazon Virtual Private Cloud (Amazon VPC) is a service that lets you launch AWS resources in a logically isolated virtual network that you define. You have complete control over your virtual networking environment, including selection of your own IP address range, creation of subnets, and configuration of route tables and network gateways. You can use both IPv4 and IPv6 for most resources in your virtual private cloud, helping to ensure secure and easy access to resources and applications.
Endpoints are virtual devices. They are horizontally scaled. redundant, and highly available VPC components that allow communication between instances in your VPC and services without imposing availability risks or bandwidth constraints on your network traffic.
There are two types of VPC endpoints:
Interface Endpoints
An interface endpoint is an elastic network interface with a private IP address that serves as an entry point for traffic destined to a supported service.
Gateway Endpoints
- Amazon S3
- DynamoDB
VPC Private Link
If you see a question asking about peering VPCs to tens, hundreds, or thousands of customer VPCS, think of AWS Private Link.
- It doesn’t require VPC peering; no route tables, NAT, IGWs, etc.
- Requires a Network Load Balancer on the service VPC and an ENI on the customer VPC.
Transit Gateway
If you are given a scenario question where it’s talking about how you can simplify your network topology, maybe you have got hundreds of VPN connections coming in, direct connection, a whole bunch of VPC peering going on and you also need to support IP multicast. I want you to think of Transit Gateway immediately.
It’s a way of simplifying your network architecture or topology, and it always uses a hub and spoke model.
- Allows you to have transitive peering between thousands of VPCs and on-premises data centers.
- Works on a hub-and-spoke model
- Works on a regional basis, but you can have it across multiple regions.
- You can use it across multiple AWS accounts using RAM (Resource Access Manager).
- You can use route tables to limit how VPCs talk to one another.
- Works with Direct Connect as well as VPN connections.
- Supports IP multi-cast (not supported by any other AWS service)
VPN CloudHub
If you see a scenario talking about how you can essentially manage your multiple sites with VPN, please definitely consider VPN CloudHub.

- If you have multiple sites, each with it’s own VPN connection, you can use AWS VPN CloudHub to connect those sites together.
- Hub-and-spoke model.
- Low cost; easy to manage.
- It operates over the public Internet, but all traffic between the customer gateway and the AWS VPN CloudHub is encrypted.
Networking Costs on AWS
If you see a scenario based question where it’s talking about cost optimization, you always want to use private IPs over public IPs
- Using private IP addresses will utilizes the AWS backbone network which will save on costs.
- If you want to cut all network costs, group your EC2 instances in the same Availability Zone and use private IP addresses. This will be cost-free, but make sure to keep in mind single point of failure issues.
References
AWS Storage Blog
AWS Management & Governance Blog
Dive Into Exam
Having just created a new VPC and launching an instance into its public subnet, you realise that you have forgotten to assign a public IP to the instance during creation. What is the simplest way to make your instance reachable from the outside world?
- Answer: Create an Elastic IP and new network interface. Associate the Elastic IP to the new network interface, and the new network interface to your instance.
- Explanation: Although creating a new NIC & associating an EIP also results in your instance being accessible from the internet, it leaves your instance with 2 NICs & 2 private IPs as well as the public address and is therefore not the simplest solution. By default, any user-created VPC subnet WILL NOT automatically assign public IPv4 addresses to instances – the only subnet that does this is the “default” VPC subnets automatically created by AWS in your account.
Are you permitted to conduct your own vulnerability scans on your own VPC without alerting AWS first?
- Answer: Depends on the type of scan and the service being scanned. Some scans can be performed without alerting AWS, some require you to alert.
- Explanation: Until recently customers were not permitted to conduct penetration testing without AWS engagement. However that has changed. There are still conditions though.
True or False: You can accelerate your application by adding a second Internet gateway to your VPC.
- Answer: FALSE
- Explanation: You may have only one Internet gateway per VPC.
True or False: An application load balancer must be deployed into at least two subnets.
- Answer: True
Which of the following allows you to SSH or RDP into an EC2 instance located in a private subnet?
- Answer: Bastion host
- Explanation: A Bastion host allows you to securely administer (via SSH or RDP) an EC2 instance located in a private subnet. Don’t confuse Bastions and NATs, which allow outside traffic to reach an instance in a private subnet.
Which of the following offers the largest range of internal IP addresses?
- Answer: /16
- Explanation: The /16 offers 65,536 possible addresses.
When I create a new security group, all outbound traffic is allowed by default.
- Answer: True
By default, how many VPCs am I allowed in each AWS region?
- Answer: 5
To save administration headaches, a consultant advises that you leave all security groups in web-facing subnets open on port 22 to 0.0.0.0/0 CIDR. That way, you can connect wherever you are in the world. Is this a good security design?
- Answer: No.
- Explanation: 0.0.0.0/0 would allow ANYONE from ANYWHERE to connect to your instances. This is generally a bad plan. The phrase ‘web-facing subnets’ does not mean just web servers. It would include any instances in that subnet some of which you may not strangers attacking. You would only allow 0.0.0.0/0 on port 80 or 443 to to connect to your public facing Web Servers, or preferably only to an ELB. Good security starts by limiting public access to only what the customer needs. Please see the AWS Security whitepaper for complete details.
AWS Solution Architect(Associate) - Topic 6: VPCs
http://vincentgaohj.github.io/Blog/2021/02/07/AWS-Solution-Architect-Associate-6-VPCs/